KYC Automation Architecture: Building Scalable Verification Systems
Design patterns and implementation strategies for building automated, scalable Know Your Customer (KYC) verification systems.
Introducton
In today's fast-paced financial landscape, Know Your Customer (KYC) processes stand as both a critical compliance requirement and a significant operational challenge. Financial institutions worldwide grapple with the complexity of customer verification while trying to maintain efficiency and regulatory compliance.
Traditional KYC processes often involve manual document reviews, repetitive data entry, and time-consuming verification steps. These manual approaches not only slow down customer onboarding but also introduce inconsistencies and human errors. For many organizations, what should be a streamlined verification process becomes a bottleneck that frustrates customers and strains internal resources.
The impact of these manual processes extends far beyond simple operational inefficiencies. When customer onboarding takes days or weeks instead of minutes or hours, it directly affects customer satisfaction and can lead to abandoned applications. Financial institutions report that up to 40%[1] of potential customers abandon the onboarding process due to lengthy KYC procedures. This translates to significant lost revenue opportunities and damaged brand reputation.
Moreover, as regulatory requirements continue to evolve and become more complex, maintaining compliance through manual processes becomes increasingly challenging. Organizations must adapt to new regulations across different jurisdictions while ensuring consistent verification standards. This challenge is particularly acute for institutions operating across multiple regions, each with its own regulatory framework.
The need for scalable, automated verification systems has never been more pressing. Modern financial institutions require solutions that can handle growing transaction volumes, adapt to regulatory changes, and provide consistent verification outcomes. Automation not only addresses these operational challenges but also creates opportunities for better customer experiences and more efficient compliance processes.
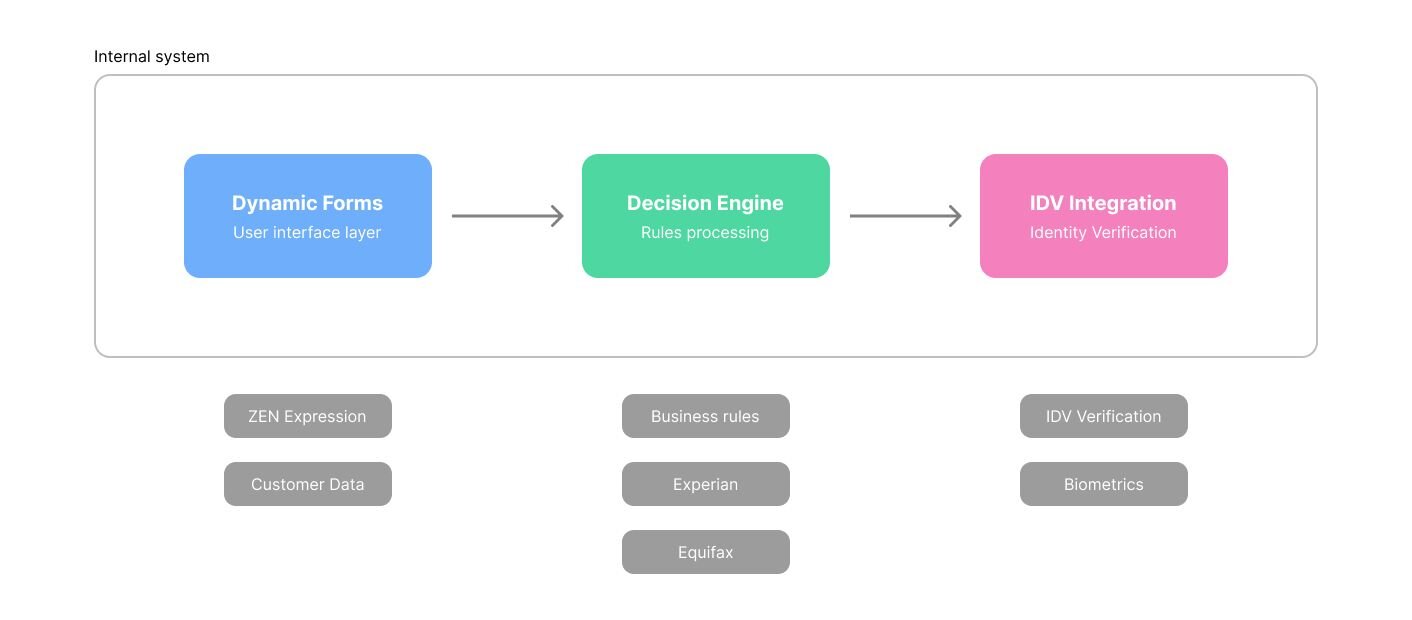
Building a scalable KYC verification system requires careful consideration of various architectural components, from dynamic form generation to automated decision-making and identity verification integration. Let's explore how these components work together to create robust, efficient KYC systems that meet both regulatory requirements and business needs.
Key Components of Modern KYC Architecture
Dynamic Form Generation
At the heart of modern KYC systems lies the shift from rigid, static forms to dynamic, intelligent interfaces that adapt to both user input and compliance requirements. Traditional forms, with their one-size-fits-all approach, often collect unnecessary information or miss crucial data points depending on the specific case. This inefficiency not only frustrates users but also complicates compliance efforts.
Dynamic form generation revolutionizes this approach by creating responsive interfaces that evolve based on context. For instance, when a customer indicates they're a corporate entity rather than an individual, the form automatically adjusts to request relevant company documentation. Similarly, when a user selects their country of operation, the form adapts to collect jurisdiction-specific information required by local regulations.
The true power of dynamic forms emerges through expression languages like GoRules ZEN. This business-friendly language enables non-technical teams to define complex form behaviors without diving into code. Consider these real-world examples of form logic:
- Validate tax ID format:
matches(taxId, "^[0-9]{2}-[0-9]{7}$")orerror("Invalid tax ID format") - Show beneficial owner fields: if
company.revenue > 1000000then show beneficialOwnerFields - Require extra documentation:
customer.riskScore > 80 ? ["proofOfFunds", "sourceOfWealth"] : ["proofOfFunds"]
One of the key advantages of GoRules ZEN is its versatility - the same expression language powers both client-side validation through WebAssembly (WASM) and server-side logic via native bindings or Rust implementation. This ensures consistent behavior and validation across your entire application stack.
Expression languages drive sophisticated validation logic that goes far beyond simple required field checks. Forms can implement complex validation rules such as ensuring company registration dates align with regulatory requirements or validating document formats based on jurisdiction. Error messages become contextual and helpful, guiding users to provide correct information rather than simply highlighting errors.
The adaptability extends to compliance requirements across different regions. A single form template can dynamically adjust its fields, validation rules, and required documentation based on the jurisdiction. This ensures that whether a customer is onboarding in Singapore, the United Kingdom, or the United States, they're presented with exactly the requirements relevant to their location.
Building these adaptive forms requires careful consideration of user experience. The goal is to make complex compliance requirements feel simple and intuitive. Fields appear or hide smoothly as users progress through the form, with clear guidance about why additional information is needed. This progressive disclosure approach prevents overwhelming users while ensuring all necessary data is collected.
Automated Decision Engine
While dynamic forms streamline data collection, automated decision engines form the backbone of intelligent KYC verification. These engines transform complex compliance requirements into structured, automated decision processes that evaluate customer information consistently and efficiently.
Business rules play a pivotal role in KYC verification by codifying regulatory requirements and risk assessment policies. Instead of burying these rules deep within application code, modern architectures leverage rules engines to maintain them separately. This separation allows compliance teams to directly manage and update verification logic without requiring software development cycles.
Consider some common verification rules in KYC processing:
- If customer revenue exceeds $10M and jurisdiction is high-risk, require enhanced due diligence
- When beneficial ownership includes politically exposed persons, escalate for manual review
- For businesses under 2 years old, require additional financial documentation
- If transaction volumes exceed historical patterns by 200%, trigger compliance review
When implementing a rules engine like GoRules, decisions become highly maintainable through visual decision modeling. Business analysts can create and modify complex verification logic using intuitive interfaces, while the engine ensures high-performance execution across thousands of verifications.
Integration of rules engines into KYC systems typically follows event-driven patterns. As customer information flows through the verification process, the rules engine evaluates data at key decision points, triggering appropriate actions or requests for additional information. This approach enables real-time decision making - crucial for modern digital onboarding experiences where customers expect immediate feedback.
The real power of automated decision engines emerges in their ability to handle complex, multi-step verification processes. They can orchestrate various checks, from simple validation rules to sophisticated risk scoring models, while maintaining clear audit trails of each decision. This not only accelerates the verification process but also provides valuable insights for compliance reporting and process optimization.
Identity Verification (IDV) Integration
The final crucial component of modern KYC systems is robust identity verification integration. While forms collect information and rules engines make decisions, identity verification services provide the critical validation of customer identities. These services have evolved from simple document validation to sophisticated multi-factor verification systems that combine document analysis, biometric matching, and data crosschecking.
Modern identity verification approaches leverage artificial intelligence and machine learning to analyze identity documents in real-time. When a customer uploads their passport or driver's license, these systems can instantly verify the document's authenticity, check for signs of tampering, and extract relevant information. This automated analysis is complemented by biometric verification, where selfie photos or video recordings are matched against ID documents to confirm the user's identity.
Integration with IDV services requires careful architectural consideration. Most organizations opt for a provider-agnostic approach, creating an abstraction layer that can work with multiple IDV providers. Here's how a typical verification flow might work:
- Document upload triggers initial automated authenticity checks
- Extracted data is cross-referenced with submitted form information
- Biometric verification confirms the user matches their documents
- Additional checks run against sanctions lists and public databases
- Results feed back into the rules engine for final verification decisions
The key to successful IDV integration lies in finding the right balance between automation and security. While automated systems can process most verifications quickly and accurately, certain cases may require manual review. The architecture should support seamless escalation to human reviewers when necessary, without disrupting the overall flow.
Managing multiple IDV providers has become a common practice, allowing organizations to optimize for different regions, document types, or verification requirements. This approach provides redundancy and helps maintain high verification success rates across diverse customer bases. The verification orchestration layer can intelligently route requests to the most appropriate provider based on factors like document type, jurisdiction, or performance metrics.
System Integration Considerations
Building a robust KYC architecture requires careful consideration of how different components interact and operate as a unified system. Modern implementations typically adopt a microservices approach, breaking down the verification process into discrete, independently deployable services that handle specific aspects of the workflow.
A well-designed KYC system orchestrates the flow of data between its components seamlessly. Form submissions trigger validation processes, feeding data into the rules engine for decision-making while simultaneously initiating identity verification checks. This choreography of services must maintain data consistency while handling the asynchronous nature of various verification steps.
Error handling becomes particularly crucial in KYC systems where verification failures or service disruptions can significantly impact customer onboarding. Robust architectures implement intelligent fallback strategies. For example, if an automated document verification service is unavailable, the system might gracefully degrade to manual review rather than completely halting the verification process.
Each component in the KYC system should implement retry mechanisms, circuit breakers, and fallback options. When primary services fail, secondary paths ensure business continuity while maintaining compliance requirements.
Comprehensive monitoring and auditing capabilities are non-negotiable in KYC systems. Organizations need visibility into every verification decision, document check, and rule evaluation. This audit trail serves multiple purposes - from troubleshooting operational issues to demonstrating regulatory compliance. Modern systems implement distributed tracing to track requests across services, combined with detailed logging of all verification steps and decisions.
Real-time monitoring also plays a crucial role in maintaining system health and identifying potential issues before they impact customers. Performance metrics, error rates, and verification success rates should be continuously monitored, with alerts configured for any anomalies that might indicate problems with specific verification steps or providers.
Future-Proofing KYC Systems
In the rapidly evolving landscape of financial regulation, future-proofing KYC systems has become a critical consideration. Organizations must build verification architectures that can adapt to new regulatory requirements without requiring complete system overhauls. This adaptability starts with design decisions that anticipate change rather than just meeting current requirements.
Regulatory changes are inevitable in the KYC space. Whether it's new documentation requirements, enhanced verification procedures, or changes in risk assessment criteria, your system must be ready to adapt. This is where the separation of concerns in the architecture proves invaluable. When business rules are managed independently through rules engines, and form behaviors are controlled through expression languages, updating verification requirements becomes a configuration change rather than a development project.
A well-designed KYC system should treat compliance requirements as dynamic parameters rather than hardcoded constraints. This approach ensures that when regulations change, updates can be implemented quickly without disrupting existing operations.
Scalability in KYC systems goes beyond handling increased transaction volumes. Modern architectures must scale across multiple dimensions - supporting new jurisdictions, accommodating different types of customers, and integrating with additional verification services. Cloud-native deployments provide the flexibility to scale components independently based on demand, ensuring cost-effective operations while maintaining performance.
The maintenance aspect of KYC systems deserves special attention. Regular updates to verification logic, integration with new identity verification providers, and ongoing performance optimizations should be possible without system downtime. Feature flags and canary deployments allow organizations to roll out changes gradually, monitoring their impact before full deployment.
Looking ahead, successful KYC systems will be those that can evolve alongside both technological advancements and regulatory requirements. Organizations should maintain close relationships with regulatory bodies, technology providers, and industry peers to stay ahead of changes and ensure their verification systems remain effective and compliant.
Conclusion
Building robust, automated KYC systems represents a significant shift from traditional manual verification processes. The combination of dynamic forms, intelligent rules engines, and integrated identity verification creates a foundation for efficient, compliant customer onboarding that can adapt to changing requirements.
The journey toward automated KYC begins with understanding your current verification bottlenecks and compliance requirements. Start small - perhaps by implementing dynamic forms or automating specific decision points - and gradually expand the system's capabilities. The modular nature of modern KYC architectures allows organizations to evolve their systems incrementally while maintaining operational continuity.
Organizations implementing automated KYC systems typically report 60-80% reduction in verification times and up to 50% decrease in operational costs. More importantly, they see significant improvements in customer satisfaction and reduced abandonment rates during onboarding.
The long-term benefits of investing in automated KYC systems extend far beyond operational efficiency. A well-designed system provides:
- Consistent compliance across all verification processes
- Rapid adaptation to regulatory changes
- Improved customer experience through faster onboarding
- Better risk management through standardized decision-making
- Comprehensive audit trails for regulatory reporting
- Reduced manual workload for compliance teams
As financial services continue to digitize and regulatory requirements evolve, automated KYC systems will become increasingly crucial for maintaining competitive advantage. Organizations that invest in flexible, scalable verification architectures today will be better positioned to handle tomorrow's compliance challenges while delivering superior customer experiences.
The key is to approach KYC automation as a strategic initiative rather than just a technical project. By focusing on adaptability, scalability, and user experience while maintaining robust compliance controls, organizations can build verification systems that deliver value well into the future.

Reshaping the Insurance Industry with Steadfast Technologies

Building Python Rules Engine: Lambda and S3
